Remote IoT VPC Network Examples: Secure & Remote Access
Are you ready to revolutionize how you manage your Internet of Things (IoT) devices?
Embracing remoteIoT VPC network examples is not just an upgrade, it's a paradigm shift in the way you interact with your IoT systems, offering unparalleled security, scalability, and efficiency.
The digital landscape is rapidly evolving, and at the heart of this transformation lies the Internet of Things (IoT). From smart homes to industrial automation, IoT devices are becoming integral to our daily lives and business operations. However, as the number of connected devices grows exponentially, so does the need for secure, efficient, and easily manageable network infrastructure. This is where remoteIoT VPC (Virtual Private Cloud) network examples come into play, offering a robust solution to the challenges of modern IoT deployments.
This guide will delve into the intricacies of remoteIoT VPC networks, exploring architecture, security considerations, and best practices. Whether you are a tech enthusiast experimenting with Raspberry Pi or a seasoned professional architecting enterprise-level IoT solutions, a thorough understanding of these concepts is paramount. The ability to manage your IoT ecosystem remotely, securely connecting devices, and ensuring data privacy is no longer a luxury; it's a necessity.
| Aspect | Details |
|---|---|
| What is RemoteIoT? | RemoteIoT refers to the ability to manage and control Internet of Things (IoT) devices from a remote location. This includes monitoring, configuring, and troubleshooting devices without requiring physical access. |
| What is VPC? | VPC stands for Virtual Private Cloud. It is essentially a private network within a public cloud provider (such as AWS) that allows you to host your resources in an isolated environment. |
| Why Combine RemoteIoT and VPC? | Combining RemoteIoT with VPC provides a secure, scalable, and manageable solution for accessing and controlling IoT devices. VPCs offer a private, isolated network, ensuring data security and efficient connectivity, while RemoteIoT provides the remote access capabilities. |
| Benefits of using RemoteIoT VPC Networks |
|
| Key Components of a RemoteIoT VPC Network |
|
| Use Cases |
|
| Best Practices |
|
| Reference | AWS VPC Documentation (This is an example, replace with a relevant source) |
The core concept revolves around the secure and remote management of IoT devices. Think of it as having a private, controlled network within the cloud, specifically designed for your IoT devices. This is achieved through a combination of technologies: RemoteIoT, which allows for remote access and management, and VPC, which provides the secure and isolated network infrastructure.
For those new to this, lets clarify the basic components. RemoteIoT, in essence, provides the ability to manage IoT devices from anywhere. Whether it's a Raspberry Pi in your home lab or sensors deployed across a vast industrial complex, RemoteIoT offers the tools to monitor, control, and troubleshoot these devices without needing to be physically present. On the other hand, VPC (Virtual Private Cloud) acts as a private network within a public cloud provider like Amazon Web Services (AWS). A VPC allows you to create subnetworks, configure IP ranges, and establish communication pathways, all within a controlled environment.
By combining RemoteIoT with VPC, you create a powerful solution. You gain the ability to remotely access your devices while maintaining a high level of security and control. The VPC ensures that all traffic is contained within a private network, minimizing the risk of unauthorized access. This is particularly valuable for businesses leveraging the Internet of Things, where data security and operational efficiency are paramount.
The benefits extend beyond security. A well-designed RemoteIoT VPC network provides scalability, allowing you to easily add more devices as your IoT ecosystem grows. It also improves efficiency, as you can manage and monitor your devices remotely, reducing the need for on-site IT support. Furthermore, it offers cost-effectiveness by reducing the reliance on physical infrastructure and streamlining operational processes.
For those working with Raspberry Pi and other IoT devices, RemoteIoT VPC networks offer a particularly compelling solution. You can securely connect your Raspberry Pi devices from anywhere, just as if they were on a local private network. This allows for the development and deployment of secure and scalable IoT projects, opening up a world of possibilities, from smart home automation to industrial monitoring.
The term "remoteIoT VPC SSH" encapsulates a fundamental aspect of secure remote access. SSH (Secure Shell) tunneling is used to encrypt all network traffic, protecting data in transit. With an SSH tunnel, your data is shielded from prying eyes, even if someone were to intercept the traffic. This is a critical component of a secure RemoteIoT setup, ensuring that your devices and data remain protected.
Now, let's address a core question: Why should you care about RemoteIoT VPC SSH? The answer is simple: because security matters. In today's interconnected world, securing your IoT devices is not optional; its essential. A RemoteIoT VPC network with SSH provides a robust, secure pathway for managing your devices, allowing you to monitor, update, and control them without exposing them to unnecessary risks.
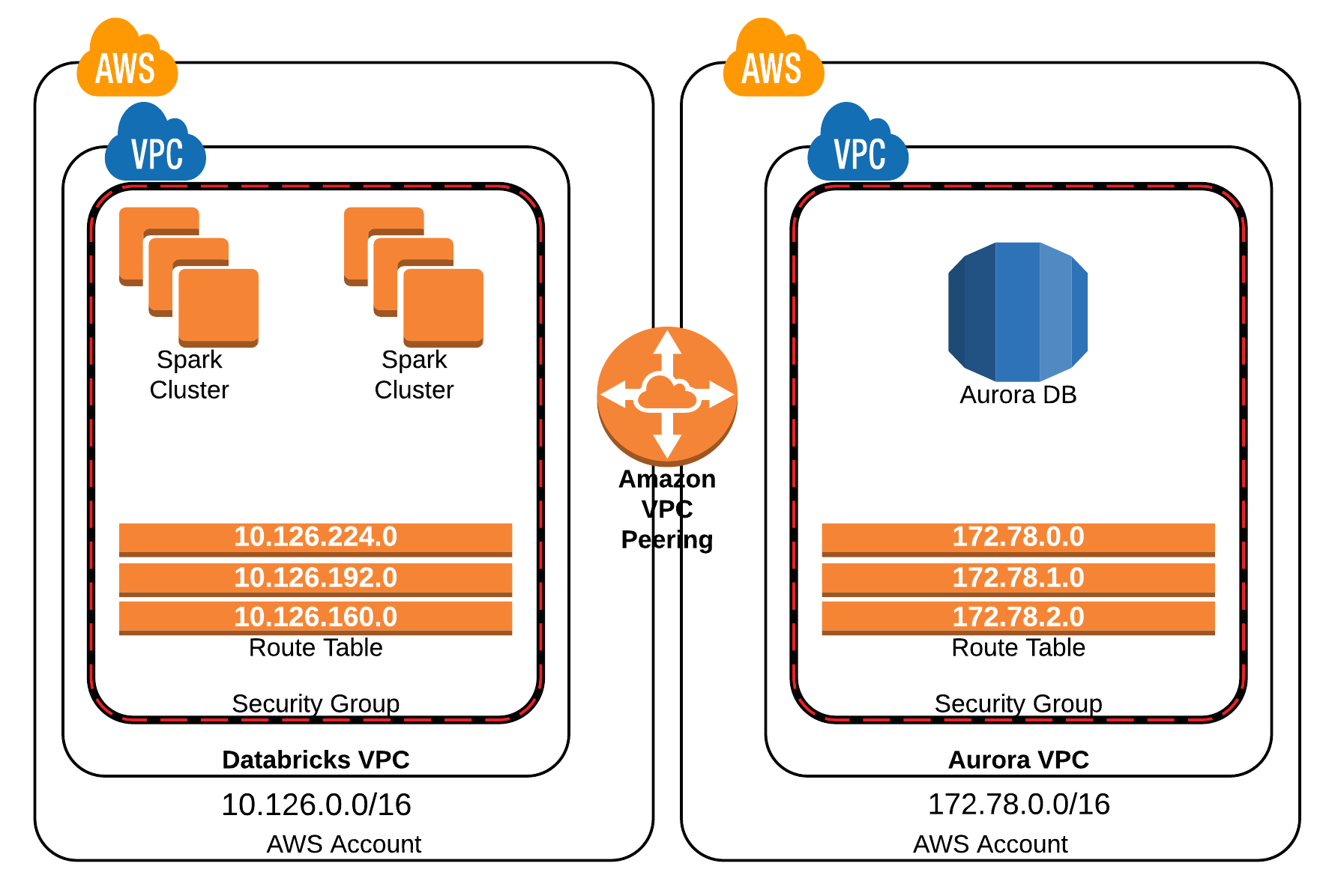
Consider the architecture of a RemoteIoT VPC network. It typically involves a VPC within a cloud provider like AWS. Within this VPC, you create subnets, which are logical divisions of your network. You also configure security groups, which act as firewalls, controlling inbound and outbound traffic. Then, you have your IoT devices, such as Raspberry Pis, connected to the network. Access to these devices is facilitated via SSH tunneling, ensuring a secure connection.
Throughout this journey, you'll learn how to configure your VPC, manage access controls, and ensure seamless communication between your devices. This involves understanding IP address ranges, security group rules, and the mechanics of SSH tunneling. A virtual local area network (VLAN) is a relevant concept here. While a VLAN operates on a different layer of the network (Layer 2), it also provides a way to logically segment a network, similar to a subnet within a VPC (Layer 3).
The journey begins with the essentials. Configuring your VPC involves setting up the network structure, specifying IP address ranges, and establishing subnetworks. Youll need to understand how to create and manage security groups to control the traffic flowing to and from your IoT devices. Managing access controls is critical. Youll need to ensure that only authorized personnel can access your devices, using strong authentication methods like passwords, multi-factor authentication, and key-based authentication for SSH.
A core part of the remoteIoT VPC tutorial involves establishing secure communication between your devices and the outside world. This is where SSH tunneling becomes vital. SSH creates an encrypted connection, ensuring that all data transmitted between your device and your remote access point is secure. This protects sensitive information from interception. Remember that all the data in the tunnel cannot be read by anyone, including RemoteIoT itself.
The remoteIoT API provides the flexibility to further automate and integrate the remoteIoT service into your system. These web services enable you to access your device from anywhere, and the support team is available to address any specific challenges. Building a secure and scalable remoteIoT VPC network example is not just beneficial; it is essential for businesses aiming to harness the potential of IoT while maintaining robust security and operational efficiency.
AWS VPC, for instance, serves as a virtual network dedicated to your AWS resources. It grants you complete control over IP address ranges, subnets, and security groups. A VPC network offers an ideal solution by providing a private, isolated environment to ensure data security and efficient connectivity.
As you delve deeper into the implementation, you will encounter best practices and strategies. Implement robust security measures, regularly update your devices, and monitor network traffic for suspicious activity. Encryption is also a critical element, guaranteeing that all data in transit is protected. Access controls limit access, and that is a fundamental requirement in a secure network.
The concept of an IoT Virtual Private Cloud (VPC) is pivotal. An IoT VPC is a private cloud environment specifically designed for IoT applications within the cloud. It provides an isolated network, ensuring the privacy and protection of data from IoT devices. The world of cloud computing and VPC networks has revolutionized how businesses and individuals manage their IT infrastructure, and RemoteIoT VPC network examples provide a robust solution for secure and scalable cloud networking.
Leveraging VPC technology allows organizations to create isolated environments within the cloud, safeguarding data privacy and ensuring efficient resource management. RemoteIoT allows for secure connection and management of machines and devices from any location, even those behind firewalls. All network traffic is encrypted via an SSH tunnel, ensuring complete data security, even from RemoteIoT itself.
Understanding the significance of a remoteIoT VPC network example is critical for businesses and individuals seeking to optimize their IoT infrastructure. The knowledge gained is essential for anyone keen on securing and managing their IoT devices. By embracing these concepts and techniques, you're not just building a connection; you're constructing a secure, scalable, and efficient network capable of handling the demands of modern IoT devices.
So, what are the main takeaways? You now have a better understanding of what makes RemoteIoT VPC network examples a game-changer. You are aware of the critical importance of these networks, and you've been given practical tips to secure your IoT infrastructure. It is about creating a secure and efficient pathway for accessing and controlling your devices. It is about taking charge of your IoT ecosystem and unlocking its full potential, all while ensuring the highest levels of security and efficiency.